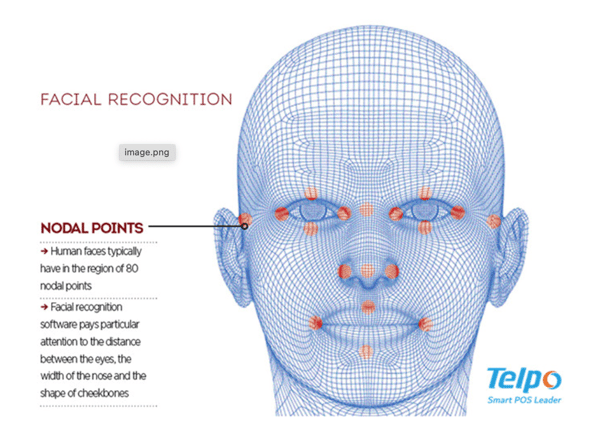
The Futurama exhibit of 1964 promised a world of technology where it would be a savior to humanity, but that optimism presented back in the day feels underwhelming as technology progresses. The visuals in Mad World show a world that's dominated by a broken, technology obsessed society, where there is no empathy or care. Steve Cutts' Man shows us further that there should be no optimism, as he shows humanity's reckless exploitation of the planet enabled by technology.
My relationship with technology would be considered a work in progress. It's a powerful tool to have, where my phone gives me access to global news, academic research, and any sort of social media my heart desires. The internet is a tool that changed lives and the way as we, a society, function as a whole, but there's a catch to this wonderful tool. Ive lost meaningful hours of my life doom scrolling, chasing dopamine hits from likes and followers. Studies show a connection from rising youth suicide rates to the use of technology, more specifically the cyberbullying behind it. I worry that myself and others aren't in control of their lives anymore, as technology and the internet dictates my attention and what I do rather than the other way around. To combat this, I try and set limits: no screens after 10:30pm and instead, I read a section of my book for 30 minutes to wind down. I also fact-check everything I see online, as you don't know what's real and what's fake, and some of those news articles can instill serious anxiety.

Technology when it comes to my friend and family, I would still say its a mixed connection, but I do value it more than it being in my free time. Sometimes for me, it's a lifeline, a connection where I get to talk to my mom and my dad from hundreds of miles away, talk to my boyfriend over long breaks, and keep connected with my friends back home on social media. My parents also use apps such as the health app, that's connected to their smartwatch, to track their health which is seriously important. Although, my friends have expressed some downsides with technology, often feeling anxious when posting stuff on social media. Technology can erode a simple hang out, often turning a connection that should have all the attention of the participants, into a photo op and status update. Technology is able to connect us in unimaginable ways, but it also has the power to disconnect us from what matters most.
Googling myself, nothing of mine popped up. I am currently not that invested on LinkedIn, so my profile does not show up as I have barely set it up just yet, but no social medias or pictures show up. I think this is good because if a job were to look me up, nothing of sorts comes up that would put me into bad standing with them. I think once I get my LinkedIn figured out, I will be smooth sailing for my digital footprint. Being intentional online can be both an opportunity and a liability, because in an age where technology rules everything, you have to be smart with your presence online.
Our relationship with technology requires attention. For me, it's about using it purposefully and attentively, making sure that I stay in control. For society, it's about being able to use it for its potential while also staying aware of the harms. Technology can be a partner but it can also be our enemy if we let it.
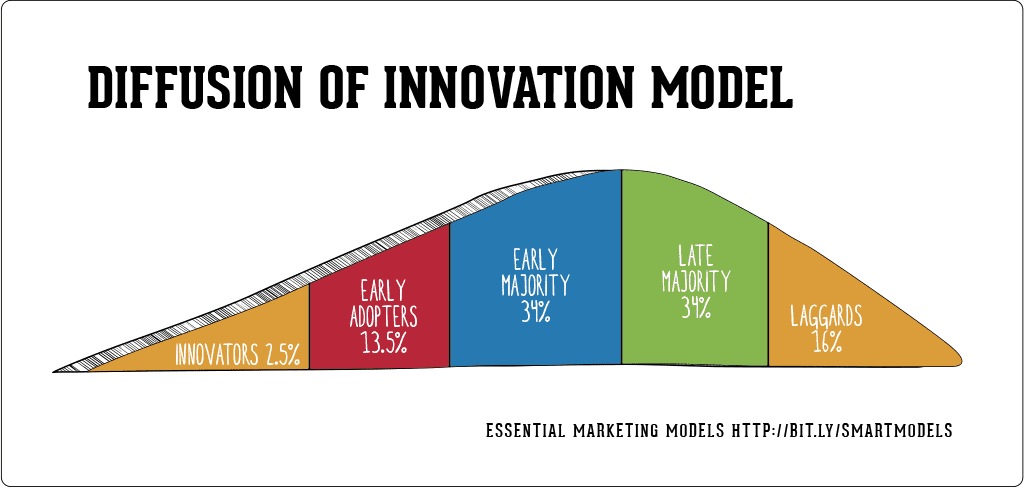
-min.jpg?width=1200&height=800&name=TXT-688-blog%201-1%20(1)-min.jpg)