
Facial Recognition technology is a software that has been around for 50+ years, with many people globally contributing to its success. In a definition made by the Department of Homeland Security, Facial recognition technology is a contemporary security solution that automatically identifies and verifies the identity of an individual from a digital image or video frame. This technology can be compared to other biometric technologies, and used for a number of activities. Although its success is made to be a team work style effort spanning over decades, the first innovator to capture the idea of facial recognition software is Woodrow W Bledsoe and his team of researchers.
Bledsoe and the researchers would run experiments through 1964-1966 to see if computers could recognize human faces. To carry out this experiment, the team would use rudimentary scanners to map out a persons eyes, nose and hairline and then see if the computer can match the same characteristics to the correct person. Unfortunately, this experiment came up unsuccessful, with Bledsoe stating: “The face recognition problem is made difficult by the great variability in head rotation and tilt, lighting intensity and angle, facial expression, aging, etc.” This is why facial recognition software became a global project, because of these difficulties, people all over the world from different times are able to put their own spin on the software and solve each one of the issues Bledsoe and his team were facing. Thanks to camera technology improvements, mapping processes, machine learning and processing speeds that were developed by other researchers, Facial Recognition has become a lot easier to achieve and use.
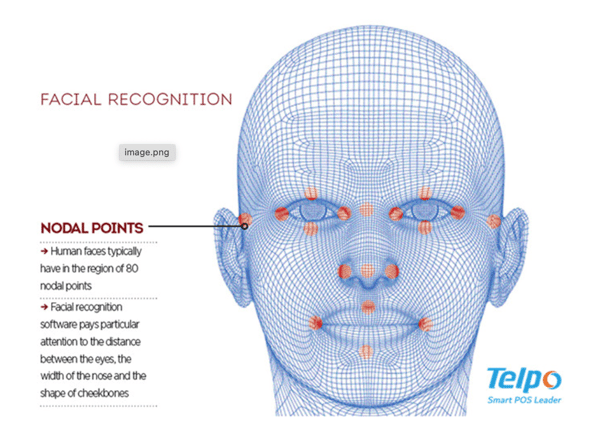
Today, we know Facial Recognition by Apple and the iPhone (although not the only facial recognition technology), generally how a successful run of facial recognition is done is the process starts off with Face detection, where the camera detects and locates an image of a face. Once the camera locates the correct face, the next step the software completes is a face analysis. This step of the program is where the software reads the geometry of your face, focusing on the key points such as the distance between your eyes, the depth of your eye sockets, the distance from forehead to chin, the shape of your cheekbones, and the contour of yours lips, ears and chin. Once the software has captured the necessary imaging required, it will then take this image and convert it to data, essentially turning your face into a mathematical formula called Faceprint. Think of Faceprint as the thumbprint to your face, this code is unique to you and is almost impossible to recreate. This faceprint is what is compared to multiple databases in order to find a match.
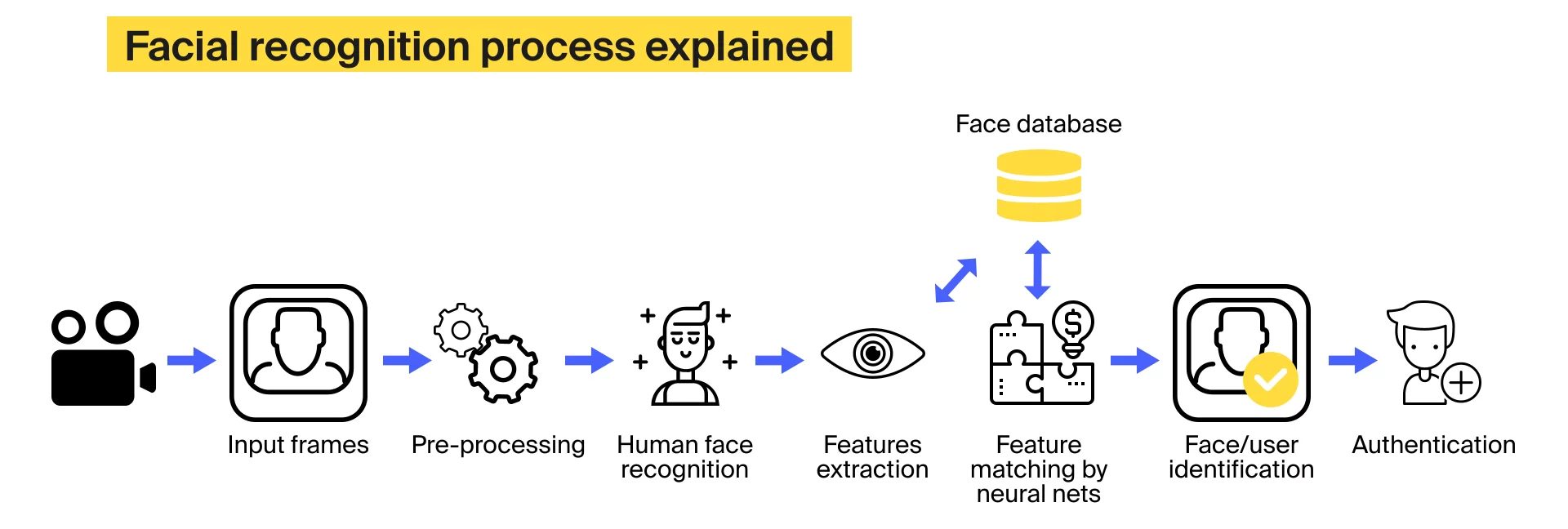
Technology that recognizes a person from their iris or thumbprint is slowly going out of style due to facial recognition being so natural and convenient. Nobody can recognize a person from their thunbprint or iris, but a picture of someone's face says a thousand words. Due to this convenience, this technology is used for a multitude of things, such as:
- Unlocking phones: Used in smartphones like iPhones to protect data and prevent unauthorized access.
- Law enforcement: Used to match mugshots with databases and identify suspects in the field via mobile devices.
- Airports and Border control: Speeds up travel with biometric passports and enhances security at checkpoints and events.
- Finding missing persons: Helps locate missing individuals by matching faces in public spaces to databases.
- Reducing retail crime: Identifies known criminals entering stores, helping prevent theft and fraud.
- Improving retail experience: Recognizes returning customers to suggest products or enable quick checkout via “face pay.”
- Banking: Allows secure, password-free transaction authorization through face scans.
- Marketing and advertising: Tracks customer reactions to ads or products and tailors content using facial cues.
- Healthcare: Used for patient ID, emotion detection, and ensuring medication adherence.
- Tracking student or worker attendance: Scans faces to log attendance in schools and workplaces.
- Increased security: Helps identify criminals and locks personal devices or home systems securely.
- Reduced crime: Deters petty crime and secures systems by replacing hackable passwords.
- Greater convenience: Enables contactless payments and fast, seamless identity checks.
- Faster processing: Verifies identity in seconds, aiding both security and efficiency.
- Integration with other technologies: Works well with existing systems, reducing setup costs.
- Surveillance: Can enable mass tracking of innocent people, raising fears of restricted freedom.
- Scope for error: Mistaken identity is possible due to camera angles or appearance changes.
- Breach of privacy: Faces can be stored without consent, sparking ethical and legal concerns.
- Massive data storage: Requires large, costly data sets that small companies may struggle to manage.
- Limiting what you share online
- Wearing clothing that may interfere with cameras, such as hats or reflective material
- Adjusting the privacy settings on your device to not include facial recognition
- Staying aware of your surroundings
- Stay up to date and speak up about the concerns
No comments:
Post a Comment